<< Go back to the Research page.
Software Bill of Materials (SBOM)
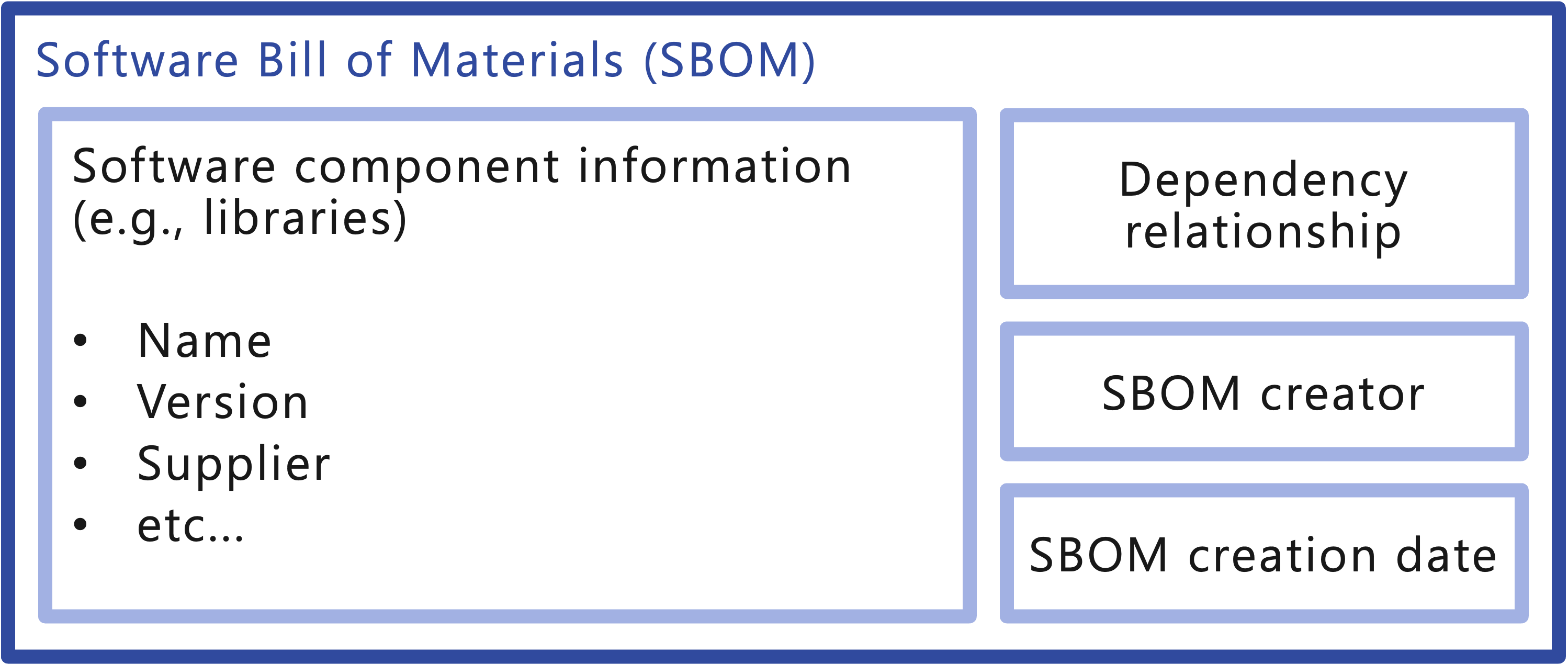
SBOM is a formal and machine-readable record of software components (e.g., libraries) used in building software, which includes details such as licenses, versions, and vendors of each software component, as well as information on supply chain relationships between components (Figure 1). With an SBOM, developers and users of software can easily acquire the software component information, which enables them to detect and mitigate vulnerability and licensing issues before they get problematic.
Background: Software Supply Chain
Modern software development is often accomplished not by implementing all functionalities from scratch but by leveraging numerous external libraries. This approach not only reduces development costs and shortens development cycles but also allows for the use of mature software components, leading to robust and sophisticated software. However, such activity comes with the following risks.
Cyber Security
If a vulnerability is found in an external library that the software being developed depends on, there is a risk that this could propagate to dependent projects, making them targets for attacks by malicious users. A real-world example is the critical vulnerability found in the widely adopted Java language library, Apache Log4j, known as Log4Shell (CVE-2021-44228). This discovery led developers worldwide who had incorporated this library into their software to scramble for patches (2021).
Additionally, there is a risk that developers of external libraries on which the software depends could intentionally introduce malicious code, or that they themselves could fall victim to hostile compromise by malicious individuals. For instance, in the case of the XZ Utils library, used by OpenSSH, an incident occurred where a malicious developer embedded a backdoor targeting SSH access (2024).
Copyright
Software is subject to copyright, and while each developer licenses it with specific terms and conditions, there is a risk of legal issues arising from inadvertent violations of these conditions or from introducing libraries with conflicting license terms, leading to copyright infringement.
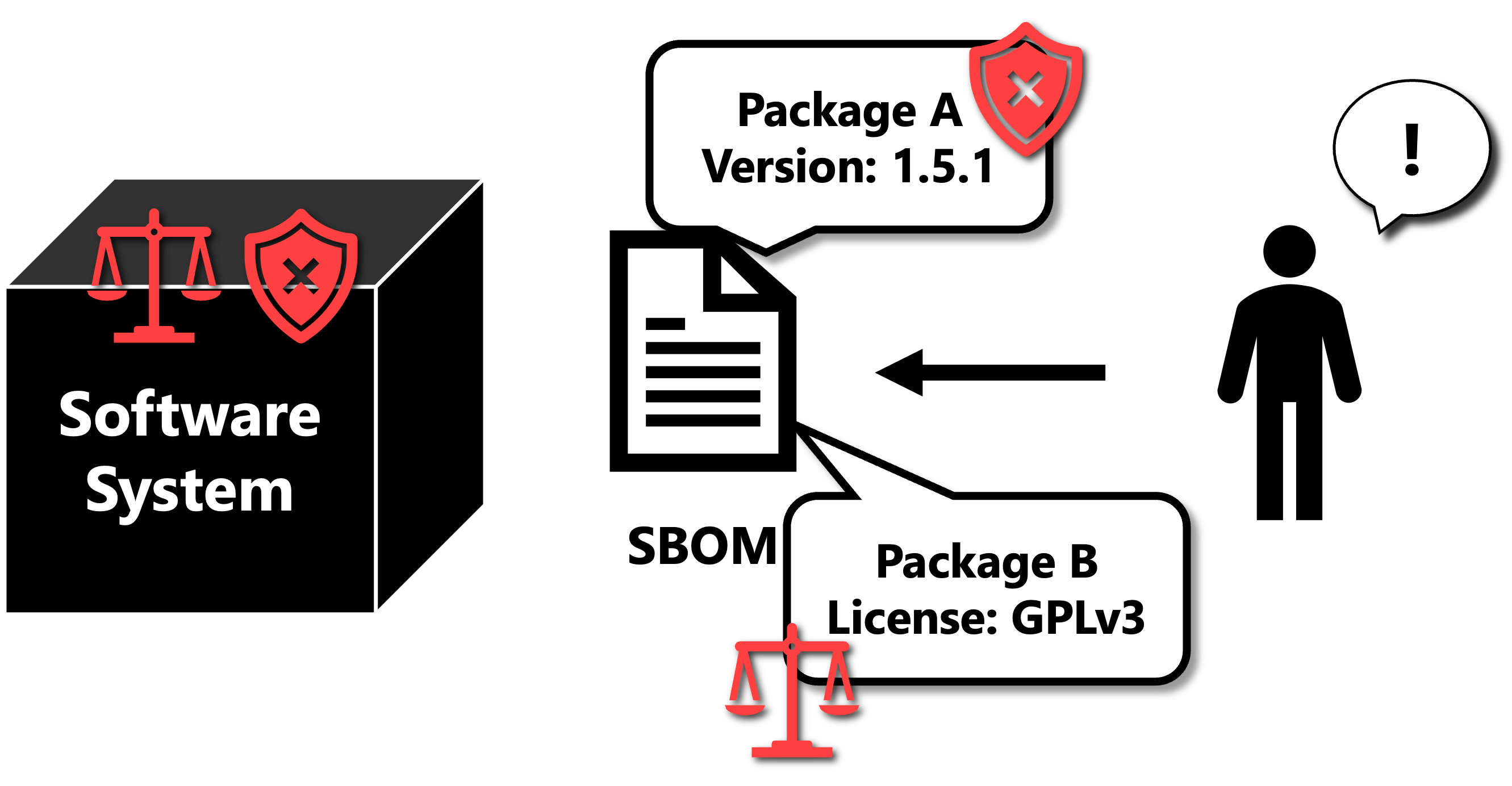
Despite identifying and addressing these risks early on is crucial, the immense number of external libraries used in current software development, especially considering transitive dependencies like dependencies of dependencies, makes proper management challenging. This emphasizes the importantance for developers and users of software to acquire the software component information through SBOMs, and to detect and mitigate vulnerability and licensing issues before they get problematic (Figure 2).
Current Status of SBOM
SPDX and CycloneDX are the primary formats for representing SBOM. SBOM is rapidly getting attention in recent years with government agencies promoting its use through Executive Order on Improving the Nation's Cybersecurity (U.S., 2021), Cyber Resilience Act (EU, 2024, most terms become effective on 2027), and SBOM Guide (Japan, published in 2023 and revised in 2024).
However, there are still many challenges to achieve the widespread adoption and practical use of SBOMs, such as the lack of effective tools for generating and utilizing SBOMs. We have been actively conducting research and technological development to address these issues. Below, we introduce two main topics of our research.
Automatic SBOM Generation
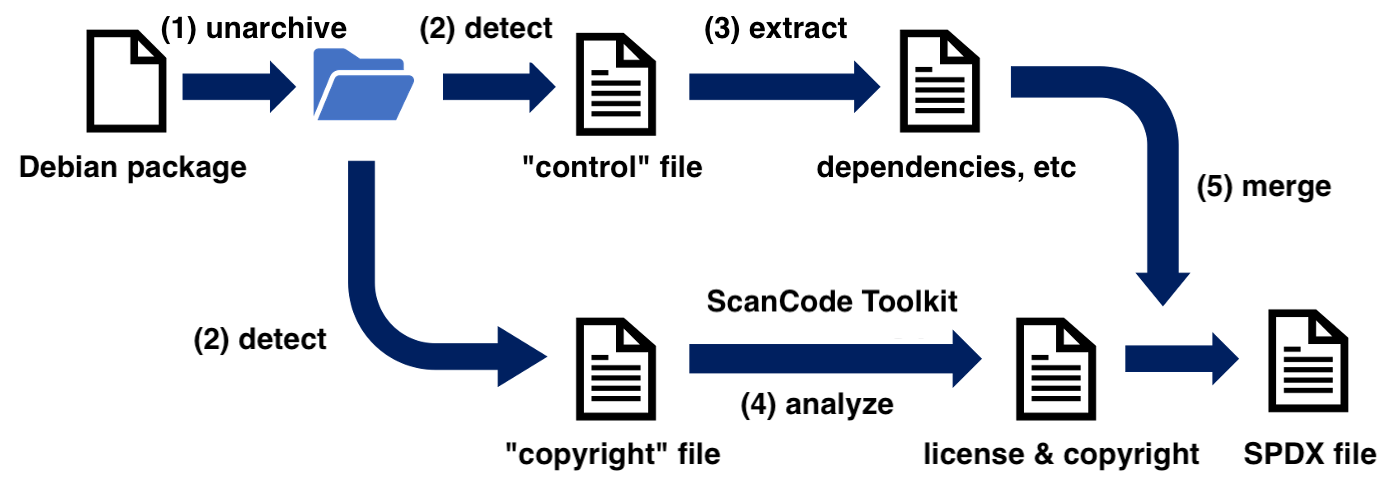
For small-scale software, it is feasible to create an SBOM manually. However, many projects, depending on their scale, utilize hundreds or even thousands of software components. In such cases, manual creation becomes impractical, so we are developing technologies to automate SBOM generation for complex software systems. Figure 3 illustrates an overview of debiantospdx, a tool that generates SPDX-format SBOMs from Debian packages.
Software Ecosystem Analysis through SBOM
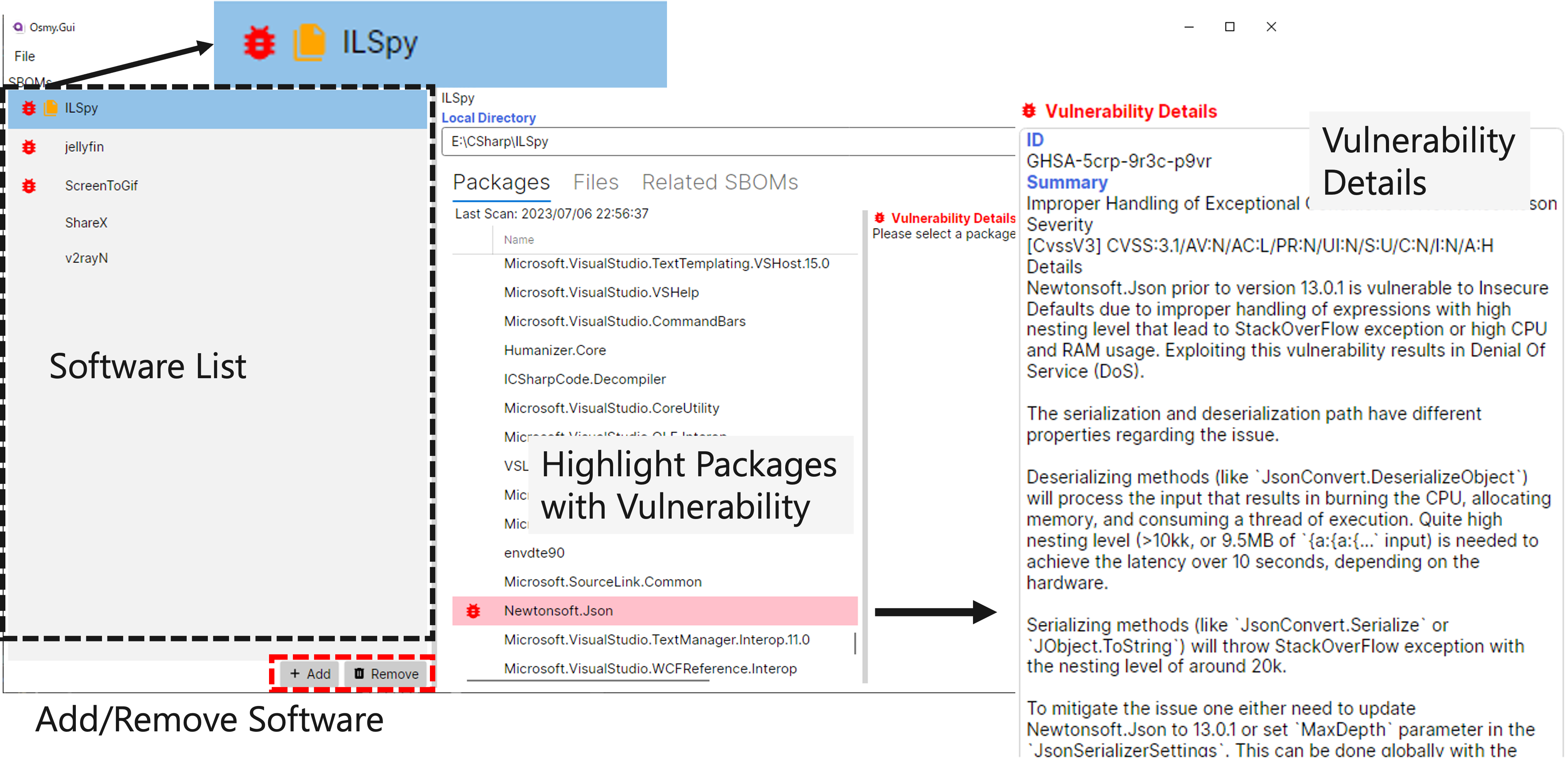
An SBOM encompasses a vast amount of component information. Manually reviewing this information is impractical; thus, tool support is essential for effective SBOM utilization. We are developing technologies to analyze SBOMs to extract information that developers and users of the software need, as well as to verify the presence of any supply chain risks. Figure 4 shows the interface of Osmy, a tool that performs vulnerability diagnostics and checksum verification from an SPDX-format SBOM.
Related Papers
- Debianパッケージ間の依存関係を表すSPDXドキュメント自動生成ツールの開発
- 田邉 傑士,神田 哲也,眞鍋 雄貴,井上 克郎,肥後 芳樹
- Osmy: A Tool for Periodic Software Vulnerability Assessment and File Integrity Verification using SPDX Documents
- Rio Kishimoto, Tetsuya Kanda, Yuki Manabe, Katsuro Inoue, Yoshiki Higo
- SBOM Challenges for Developers: From Analysis of Stack Overflow Questions
- Wataru Otoda, Tetsuya Kanda, Yuki Manabe, Katsuro Inoue, Yoshiki Higo